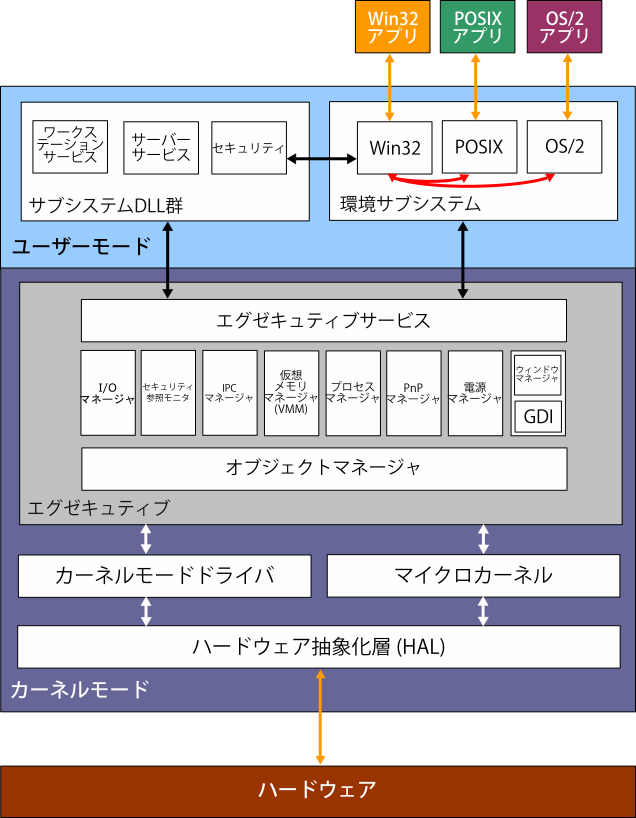
Rootkit Ntoskrnl Executive Branch
MBR rootkits, and in 6 for rootkits that manipulates the. Memory page tables of. Function located in NtosKrnl module. This function is called.
root &windows #volatility -f Win7.bin -profile=Win7SP0x86 gdtVolatility Foundation Volatility Framework 2.4CPU Sel Base Limit Type DPL Gr Pr-0 0x0 0x00000000 0x00000000 0 By Np0 0x8 0x00000000 0xffffffff Code RE Ac 0 Pg P0 0x10 0x00000000 0xffffffff Data RW Ac 0 Pg P0 0x18 0x00000000 0xffffffff Code RE Ac 3 Pg P0 0x20 0x00000000 0xffffffff Data RW Ac 3 Pg P0 0x28 0x801db000 0x000020ab TSS32 Busy 0 By P0 0x30 0x8292ec00 0x00003748 Data RW Ac 0 By P.

Once identified the correct profile, we can start to analyze the processes in the memory and, when the dump come from a windows system, the loaded DLLs. PslistTo list the processes of a system, use the pslist command. This walks the doubly-linked list pointed to by PsActiveProcessHead and shows the offset, process name, process ID, the parent process ID, number of threads, number of handles, and date/time when the process started and exited. As of 2.1 it also shows the Session ID and if the process is a Wow64 process (it uses a 32 bit address space on a 64 bit kernel).This plugin does not detect hidden or unlinked processes (but psscan can do that).If you see processes with 0 threads, 0 handles, and/or a non-empty exit time, the process may not actually still be active.For more information, see. Below, you’ll notice regsvr32.exe has terminated even though its still in the “active” list.Also note the two processes System and smss.exe will not have a Session ID, because System starts before sessions are established and smss.exeis the session manager itself. PstreeTo view the process listing in tree form, use the pstree command.
This enumerates processes using the same technique as pslist, so it will also not show hidden or unlinked processes. Child process are indicated using indention and periods. $ vol.py -f /Desktop/win7trial64bit.raw -profile=Win7SP0x64 pstreeVolatility Foundation Volatility Framework 2.4Name Pid PPid Thds Hnds Time-0xfffffa80004b09e0:System 4 0 78 489 2012-02-22 19:58:20. 0xfffffa8000ce97f0:smss.exe 208 4 2 29 2012-02-22 19:58:200xfffffa8000c006c0:csrss.exe 296 288 9 385 2012-02-22 19:58:240xfffffa8000c92300:wininit.exe 332 288 3 74 2012-02-22 19:58:30. 0xfffffa8000c5eb30:services.exe 428 332 6 193 2012-02-22 19:58:32. 1800 428 12 757 2012-02-22 20:02:26. 0xfffffa80007d09e0:svchost.exe 916 428 19 443 2012-02-22 19:58:43.
0xfffffa8000a4f630:svchost.exe 1432 428 12 350 2012-02-22 20:04:14. 0xfffffa800094d960:wlms.exe 1264 428 4 43 2012-02-22 20:02:11. 0xfffffa:sppsvc.exe 816 428 5 154 2012-02-22 19:58:41.
Rootkit Ntoskrnl Executive Branch Search
0xfffffa8000e86690:spoolsv.exe 1076 428 12 271 2012-02-22 20:02:10. 0xfffffa8001296b30:svchost.exe 568 428 10 352 2012-02-22 19:58:34. 0xfffffa8000a03b30:rundll32.exe 2016 568 3 67 2012-02-22 20:03:16. PsscanTo enumerate processes using pool tag scanning ( POOLHEADER), use the psscan command. This can find processes that previously terminated (inactive) and processes that have been hidden or unlinked by a rootkit. The downside is that rootkits can still hide by overwriting the pool tag values (though not commonly seen in the wild). $ vol.py -profile=Win7SP0x86 -f win7.dmp psscanVolatility Foundation Volatility Framework 2.0Offset Name PID PPID PDB Time created Time exited-0x3e025ba8 svchost.exe 1116 508 0x3ecf1220 2010-06-16 15:25:250x3e04f070 svchost.exe 1152 508 0x3ecf1340 2010-06-16 15:27:400x3e144c08 dwm.exe 1540 832 0x3ecf12e0 2010-06-16 15:26:580x3e145c18 TPAutoConnSvc.
DlllistTo display a process’s loaded DLLs, use the dlllist command. It walks the doubly-linked list of LDRDATATABLEENTRY structures which is pointed to by the PEB’s InLoadOrderModuleList. DLLs are automatically added to this list when a process calls LoadLibrary (or some derivative such as LdrLoadDll) and they aren’t removed until FreeLibrary is called and the reference count reaches zero. The load count column tells you if a DLL was statically loaded (i.e. As a result of being in the exe or another DLL’s import table) or dynamically loaded.
$ vol.py -f /Desktop/win7trial64bit.raw -profile=Win7SP0x64 getsidsVolatility Foundation Volatility Framework 2.4System (4): S-1-5-18 (Local System)System (4): S-1-5-32-544 (Administrators)System (4): S-1-1-0 (Everyone)System (4): S-1-5-11 (Authenticated Users)System (4): S-1-16-16384 (System Mandatory Level)smss.exe (208): S-1-5-18 (Local System)smss.exe (208): S-1-5-32-544 (Administrators)smss.exe (208): S-1-1-0 (Everyone)smss.exe (208): S-1-5-11 (Authenticated Users)smss.exe (208): S-1-16-16384 (System Mandatory Level)snip. CmdscanThe cmdscan plugin searches the memory of csrss.exe on XP/2003/Vista/2008 and conhost.exe on Windows 7 for commands that attackers entered through a console shell (cmd.exe). This is one of the most powerful commands you can use to gain visibility into an attackers actions on a victim system, whether they opened cmd.exe through an RDP session or proxied input/output to a command shell from a networked backdoor.This plugin finds structures known as COMMANDHISTORY by looking for a known constant value (MaxHistory) and then applying sanity checks. It is important to note that the MaxHistory value can be changed by right clicking in the top left of a cmd.exe window and going to Properties. The value can also be changed for all consoles opened by a given user by modifying the registry key HKCUConsoleHistoryBufferSize. The default is 50 on Windows systems, meaning the most recent 50 commands are saved. You can tweak it if needed by using the — maxhistory=NUMBER parameter.The structures used by this plugin are not public (i.e.
Microsoft does not produce PDBs for them), thus they’re not available in WinDBG or any other forensic framework. They were reverse engineered by Michael Ligh from the conhost.exe and winsrv.dll binaries.In addition to the commands entered into a shell, this plugin shows:. The name of the console host process (csrss.exe or conhost.exe). The name of the application using the console (whatever process is using cmd.exe). The location of the command history buffers, including the current buffer count, last added command, and last displayed command. The application process handleDue to the scanning technique this plugin uses, it has the capability to find commands from both active and closed consoles. ConsolesSimilar to cmdscan the consoles plugin finds commands that attackers typed into cmd.exe or executed via backdoors.
However, instead of scanning for COMMANDHISTORY, this plugin scans for CONSOLEINFORMATION. The major advantage to this plugin is it not only prints the commands attackers typed, but it collects the entire screen buffer (input and output). For instance, instead of just seeing “dir”, you’ll see exactly what the attacker saw, including all files and directories listed by the “dir” command.Additionally, this plugin prints the following:. The original console window title and current console window title.
The name and pid of attached processes (walks a LISTENTRY to enumerate all of them if more than one). Any aliases associated with the commands executed.
For example, attackers can register an alias such that typing “hello” actually executes “cd system”. Keygen for mac torrent. The screen coordinates of the cmd.exe consoleHere’s an example of the consoles command.
Below, you’ll notice something quite funny. The forensic investigator seems to have lost his mind and cannot find the dd.exe tool for dumping memory. Nearly 20 typos later, he finds the tool and uses it. PrivsThis plugin shows you which process privileges are present, enabled, and/or enabled by default.
You can pass it the — silent flag to only show privileges that a process explicitly enabled (i.e. That were were not enabled by default but are currently enabled). The — regex=REGEX parameter can be used to filter for specific privilege names.
EnvarsTo display a process’s environment variables, use the envars plugin. Typically this will show the number of CPUs installed and the hardware architecture (though the output is a much more reliable source), the process’s current directory, temporary directory, session name, computer name, user name, and various other interesting artifacts.

VerinfoTo display the version information embedded in PE files, use the verinfo command. Not all PE files have version information, and many malware authors forge it to include false data, but nonetheless this command can be very helpful with identifying binaries and for making correlations with other files.This plugin only supports printing version information from process executables and DLLs, but later will be expanded to include kernel modules. If you want to filter by module name, use the — regex=REGEX and/or — ignore-case options. $ vol.py -f /Desktop/win7trial64bit.raw -profile=Win7SP0x64 verinfoVolatility Foundation Volatility Framework 2.4SystemRootSystem32smss.exeC:WindowsSYSTEM32ntdll.dll C:Windowssystem32csrss.exeFile version: 6.1.7600.16385Product version: 6.1.7600.16385Flags:OS: Windows NTFile Type: ApplicationFile Date:CompanyName: Microsoft CorporationFileDescription: Client Server Runtime ProcessFileVersion: 6.1.7600.16385 (win7rtm.0)InternalName: CSRSS.ExeLegalCopyright: xa9 Microsoft Corporation. All rights reserved.OriginalFilename: CSRSS.ExeProductName: Microsoftxae Windowsxae Operating SystemProductVersion: 6.1.7600.16385 snip. EnumfuncThis plugin enumerates imported and exported functions from processes, dlls, and kernel drivers.
Rootkit Ntoskrnl Executive Branch Tx
Specifically, it handles functions imported by name or ordinal, functions exported by name or ordinal, and forwarded exports. The output will be very verbose in most cases (functions exported by ntdll, msvcrt, and kernel32 can reach 1000+ alone). So you can either reduce the verbosity by filtering criteria with the command-line options (shown below) or you can use look at the code in enumfunc.py and use it as an example of how to use the IAT and EAT parsing API functions in your own plugin. For example, the plugin leverages the imports and exports APIs to find functions in memory when checking for hooks.Also note this plugin is in the contrib directory, so you can pass that to — plugins like this: $ vol.py -plugins=contrib/plugins/ -f /Desktop/win7trial64bit.raw -profile=Win7SP0x64 enumfunc -h.-s, -scan Scan for objects-P, -process-only Process only-K, -kernel-only Kernel only-I, -import-only Imports only-E, -export-only Exports onlyTo use pool scanners for finding processes and kernel drivers instead of walking linked lists, use the -s option. This can be useful if you’re trying to enumerate functions in hidden processes or drivers.